This Gmail Scam Is Fooling Even Tech-Savvy Users
We still haven’t finished reeling from the last internet scam that attempted to hack all that we know dear (aka Netflix), and now there’s a new one in our midst.
The latest scam is targeting Google’s email platform, Gmail, and it is frighteningly effective at stealing your passwords. And, apparently, it’s been happening for months.
According to an article from Fortune, the scheme has been growing in popularity since late last year and has attacked other email services in addition to Gmail. And if you think you’re tech savvy enough to avoid these types of scams, think again.
A report from researchers at WordFence, which works on security for the popular blogging site WordPress, warned all email users. The team expressed caution, saying that the scam has had “a wide impact, even on experienced technical users.”
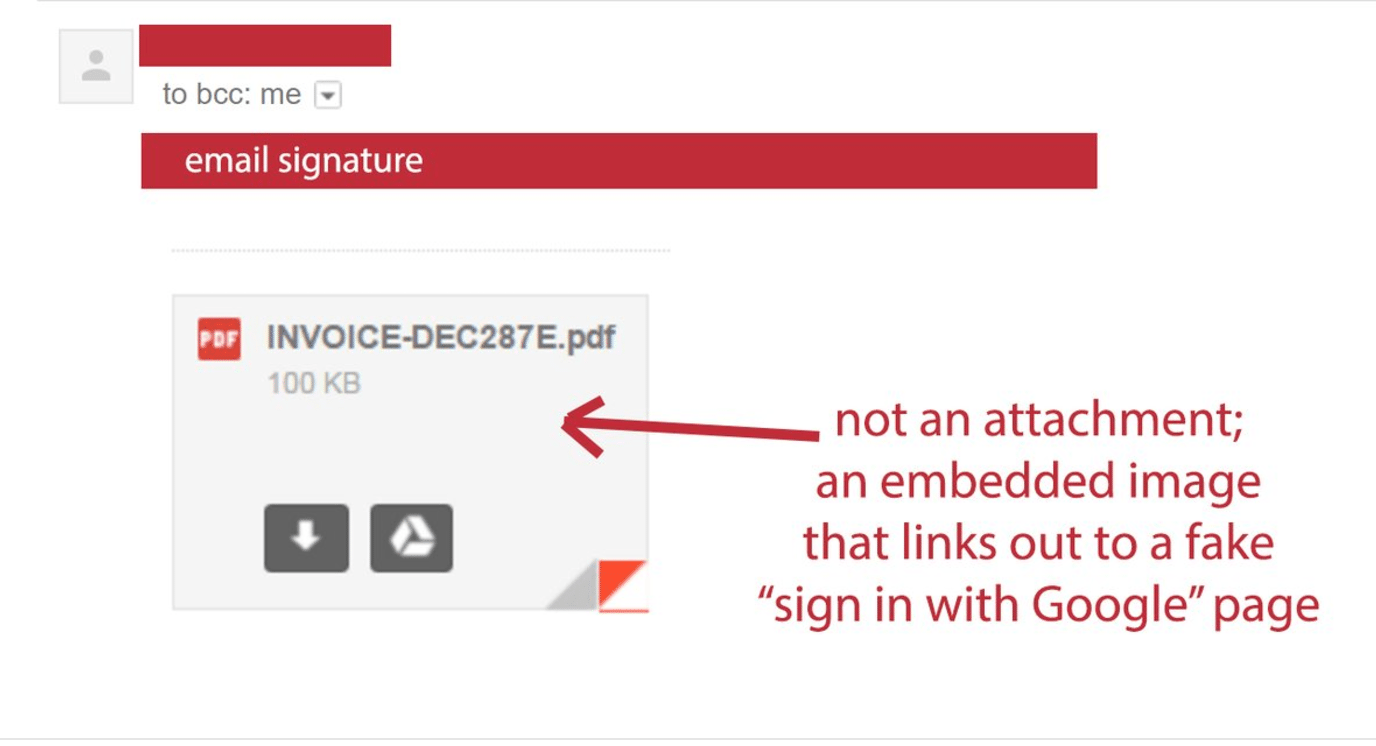
So how does this incredibly effective scam work? Well, it all starts with a simple attachment—or so it seems.
https://twitter.com/tomscott/status/812265182646927361
The attacker is disguised as a known contact and sends a trap email to the victim. That email contains an attachment that appears to be a PDF or Word document. Everything seems to be normal. This is where things get bad.
The attachment isn’t really an attachment at all—it’s an embedded image that appears to be a PDF or a Word Document. Instead of showing a preview of the “document” when clicked, the embed links to a fake Google login page. If you can see where this is going, you’ll know it’s really conniving.
The sign-in page appears to be legit. It has the Google logo, an exact replica of the username and password entry fields, the Google slogan (“One account. All of Google.”) and everything else. It looks perfect—except for one tiny detail: the URL.
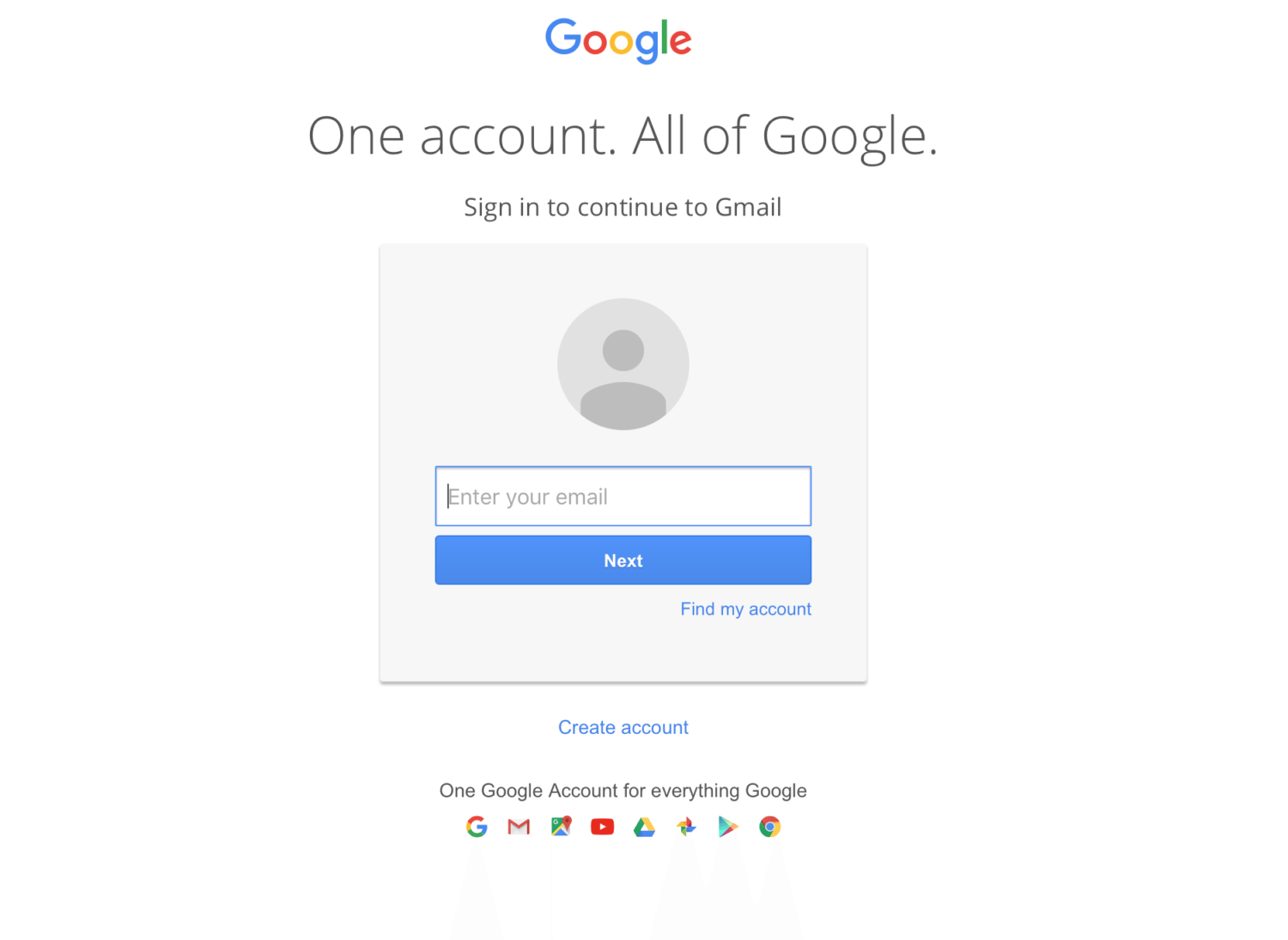
Though the URL still contains the seemingly-legit “google.com,” it’s preceded by this odd little bit of code: “data:text/html.”
And according to Fortune, the text in the address bar makes the page “data URI,” not a URL. This means a file gets embedded, instead of identifying where a website is located on the web. If you zoom out on the address bar, you can see a long string of random characters. This is the web script that makes the file look like the Gmail login, and this is how they get you.

As soon as you enter your username and password, it’s all over. The hackers can access all your information, your inbox and your contacts. From there, they send the scam onto someone else in your contacts list. They can create legitimate-sounding email subjects and use past emails and attachments to create hijacked versions that will hack the next person’s account.
If this sounds scary to you, that’s because it is. But it’s easy to protect yourself. Don’t open any attachments unless you verify who they’re from and why they have sent them. If you use Google Chrome, check the address bar and make sure the green lock symbol appears before you enter any personal info into a website. And make sure that green lock precedes a legitimate URL (like the one in the image above) that doesn’t have any weird extra characters added to the front of it.
Experts also recommend adding a two-step authentication to accounts and using a dedicated security token as well.